
Our education portal identifies users that show signs of potential compromise. The user demonstrates the need for additional education through the accrual of points given per action. Additionally, by monitoring tags, we can identify specific types of attacks that may be hot topics for your company.
Know where in the world your employees are clicking from. Our geographic analytics capture geographic IP data as users click.
Our phishing service is built with customers in mind. We are the most flexible platform in phishing education and regularly add customer-requested features. We will even build your entire phishing education program and deliver it for you.
At Snared we care about protecting our clients and their image. We have worked continuously to detect hundreds, even thousands of malicious attacks. We specialize in Phishing Education as we understand the first line of defense is to ensure employees can quickly and easily recognize a cyber-attack. Our goal is to develop your employees' core understandings and detection techniques to prevent phishing attacks on your company. We are confident in saying we offer the best white glove phishing education solution in our industry and pride ourselves on putting our customers first.
Get Started now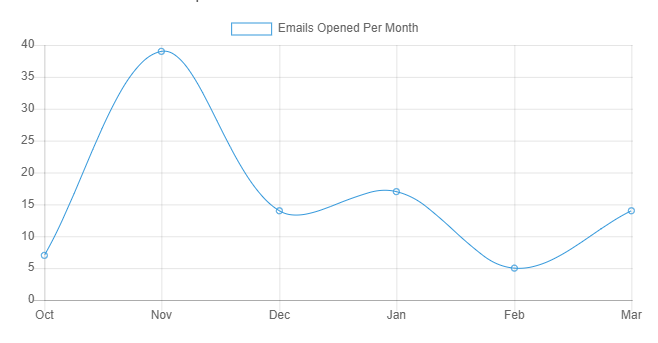
Snared was designed to change employee behavior through simulated real-life phishing campaigns. Through these campaigns Snared detects employees who show high-risk behaviors and then enrolls them in real time education simulations. Our team develops campaigns based on real phishing attempts to create accurate up to date examples that focus on what today’s threats are to a company.
Our method of phishing education focuses on imitating real phishing attacks we have recently discovered. Doing so allows our team to create campaigns that are up to date with current phishing attempts and creates critical phishing simulations that had they been real would be an active threat to a company. Through our experience, we have found many threats companies face are:
Snared is designed to automatically enroll users who have shown high-risk behaviors leading to needing more education. Each time a user clicks on a link in a phishing email or submits credentials in a harvesting attack, points are added to a user's profile. When a user reaches 20 points, they are automatically enrolled in training. The point values of each action are fully customizable to match your company's unique needs and training objectives.
We understand your time is valuable that is why at Snared we have made it very simple to get up and running with our Education Portal. Once a user list has been sent to our team we will then prepare a series of scenarios, landing pages, and attachments to run each month, we take care of the hands-on work allowing you to focus on the day to day tasks of your business.
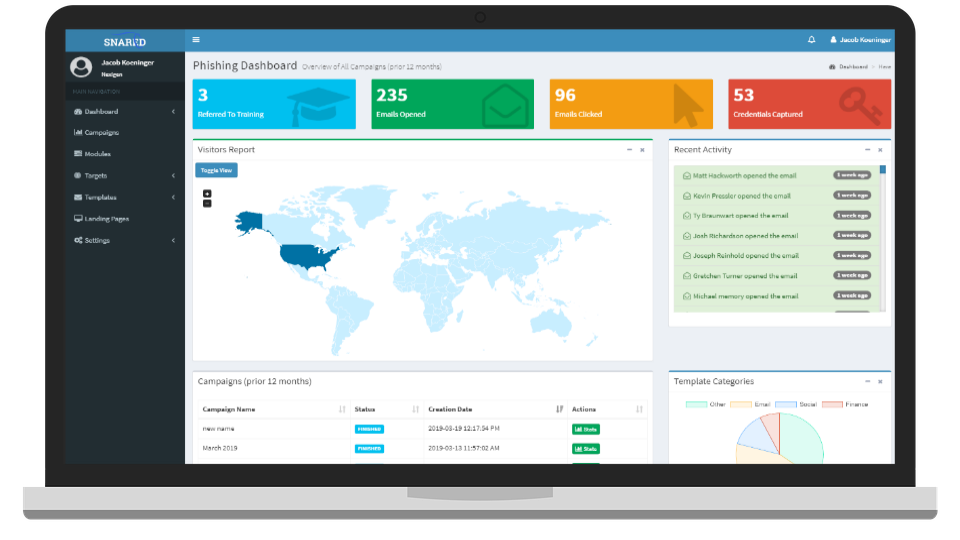
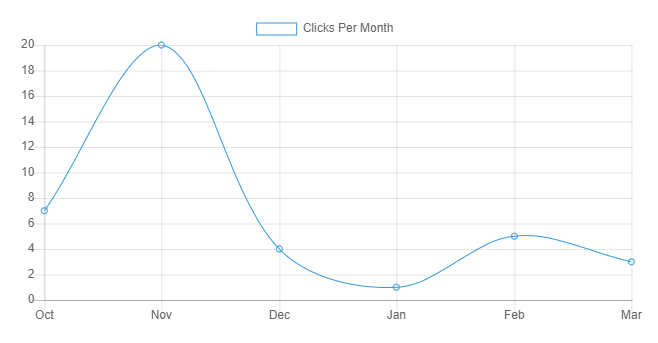
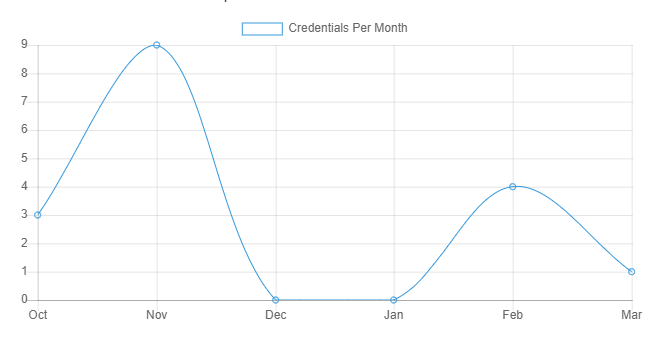
The Dashboard is where you interact with all of the features of Snared. From viewing data to managing campaigns and education, everything is available in the dashboard with no complexities or additional effort. We track statistics on historical data, user education enrollment, devices clicked from, and geographical data to give you the insights and control you need to manage your education.
The education portal is where you manage our additional education modules. This allows you to manually enroll users in a variety of educational sessions with just a few clicks.
Snared has developed a reporting system that quickly and easily provides the user with detailed information. This information provides analytics and reporting that can be quickly analyzed among executive teams to showcase the results of the phishing education campaign.
Phishing 101
A phishing attack is an attempt to steal critical information from organizations and individuals, typically in the form of usernames, passwords, credit card information, network credentials, and more. During these attacks, people appear as reputable individuals and organizations to bait victims into performing actions such as clicking on malicious links and downloading documents that encourage the victim to willingly hand over sensitive information. When an attack is successful not only is the individual at risk, the company is as well. Some of the risks for an organization include financial loss as well as reputation damage. It has been shown that many organizations that were attacked lost a significant number of customers due to reputation damage.
Typically, phishing attempts begin with a simple email requesting information that would allow the attacker insight to sensitive information through the user interaction. This interaction is used to lure the victim into providing confidential information through links and downloadable content that is believed to be safe but in fact, is malicious and infected. A few methods that are used often can be found below.
Email with links that appear legitimate at a glance, however, when looked at closely often feature subtle misspellings or utilize a subdomain.
Employs JavaScript commands to manipulate a website URL to look legitimate.
Action where attackers corrupt legitimate websites with malicious pop-up dialogue boxes that redirect users to another site where attackers can gain sensitive information.
Attackers infect documents such as .exe files, Microsoft Office files, and PDF documents manipulating the user to install ransomware or other malware without the user knowing.
It is important to know and understand that phishing attempts do not only happen via email, these attacks can also occur via phone calls, text messages, and social media.
Phishing is a very broad term it is important to understand the specific types of phishing scams and how they utilized targeted methods to attack certain individuals and organizations.
One of the most common attacks is spear phishing. Spear phishing is directed at one user instead of a group of individuals. These types of attacks are usually successful as the attacker has spent time learning the behaviors of the user as well as gathering information that helps customize the attack. Doing so typically prevents the user from questioning the source as it is designed to appear as a common source such as their bank requesting information. We have even seen attackers hijack business email communications and create highly customized messages such as posing as the companies HR representative.
In this attempt, attackers gain access to view legitimate, previously delivered email messages. After doing so they create a “clone” or simply an identical copy and then infect the attachment or create a malicious link once again tricking the user.
In this attempt, the attacker focuses their efforts on the high-profile executives in the organization. Typically, in this attempt, the attackers will present as some type of legal communication or another high-level executive business.
Education. As we stated earlier companies first line of defense is their employees. It is important for organizations to educate employees to prevent phishing attacks, specifically teaching them how to recognize suspicious emails, attachments, and links. It is also important to know and understand how quickly cyber attackers can refine their techniques, increasing the importance of continued education.
It is important to know and understand that phishing attempts do not only happen via email, these attacks can also occur via phone calls, text messages, and social media.
For several years, Eagle has been utilizing Snared's phishing program. The program highlights all the various, creative, and ever-changing ways scammers attempt to gain sensitive information via email. Early on, we had a number of people opening these fictitious emails, clicking links, and in a couple of cases, handing over credentials! Now, there exists a healthy paranoia throughout the company- to always be aware of where email is coming from. This is not to say we’ve reached perfection, or ever will, which is why we continue to utilize this service. The online portal and reporting allow us to easily track repeat offenders, and counsel and educate them further.
Extremely impressed with not only the Snared product but also the responsiveness and follow up that the Snared Team provides. Like most companies these days, cybersecurity is front and center in our organization. Phishing email scams are not only on the rise but also more and more sophisticated. Our employees are better trained and on their toes thanks to the email tests and education that the system provides. I couldn’t recommend it more!
The phishing portal Snared offers has been a great training tool for our company. We are able to show our employees how legitimate some phishing emails can look and to always be alert when opening ANY email. The ability to track who has opened the phony emails sent through the campaign and provide additional training has been great.